What Is The FAR's Cybersecurity Requirement?
Data protection and cybersecurity requirements are not a new concept - especially for anyone who has worked in the healthcare field (HIPA) or in the banking industry. So it's pretty much "business as usual" if you have formalized risk management processes in place, are ISO 27002 certified, or have been dealing with healthcare or financial data. So this series is for the 'newbies' to the requirements being enacted to protect two broad classes of information. The first is "Federal Contract Information" which is a pretty broad category and covers all government agencies and their contractors including the Department of Agriculture, Forestry, National Park Service, and any number of agencies you would have never thought were covered - but they are! The second class of information being protected is "Controlled Unclassified Information" (CUI) which although commonly associated with the Department of Defense can span across agency lines to others like Department of Energy etc.
These requirements are expressed in your contract as either of two clauses - one based on the Federal Acquisition Regulation (FAR) and the second based on the Defense Federal Acquisition Regulation System (DFARS)
These requirements are expressed in your contract as either of two clauses - one based on the Federal Acquisition Regulation (FAR) and the second based on the Defense Federal Acquisition Regulation System (DFARS)

Both of these requirements arise from a common source and both require various cyber hygiene practices by government contractors to limit possible loss of data or damage to data systems caused by malicious third parties. The essential difference is the FAR requirement is a subset of the lower end of the DFARS requirements and the FAR allows self-certification of meeting these requirements (for now). The DFARS requirements range from the same as the FAR at one end of a five-step (levels) spectrum (known as the Cybersecurity Maturity Model (CMM) to much more elaborate and detailed requirements. The DFARS is also replacing the previously allowed self-certification of compliance to a third-party certification requirement so as to ensure contractors actually meet the stated requirements.
As of this date (September 2022) the CMM Certification (CMMC) program is in its infancy and the implementation of the program is still underway. The first step has been the release of how the CMM will apportion the requirements of the National Institute of Standards and Technology’s Special Publication (SP) 800-171, Protecting Controlled Unclassified Information in Nonfederal Systems and Organizations to the five levels of CMM. This has been accomplished and the resulting CMM Framework has been publicized by the Office of the Secretary for Defense.
We are still waiting for the selection, training, and certification of the actual third party entities that will be allowed to certify compliance (CMMC) so a word of caution: Beware unscrupulous individuals who may misrepresent themselves as cybersecurity auditors who can verify your CMM Compliance. This is a time where such unscrupulous individuals will be very busy preying on unsuspecting individuals and small businesses …. Check them out before writing a check or signing a service agreement.
The second element is the requirement by the Department of Defense that contractors (and subcontractors) seeking to respond to solicitations starting in the second half of 2020 must be certified at an appropriate CMM level for that opportunity. Those who do not meet the appropriate certification (CMMC) level will not be eligible to compete.
While the FAR requirements trail behind the DoD’s CMMC initiative, many experts believe the government is likely to settle on a single program and make at least some of the CMMC requirements applicable to other organizations. This is already evident within the Department of Energy (DOE) who is looking to model their requirements more along the DoD CMM route.
While the FAR requirements trail behind the DoD’s CMMC initiative, many experts believe the government is likely to settle on a single program and make at least some of the CMMC requirements applicable to other organizations. This is already evident within the Department of Energy (DOE) who is looking to model their requirements more along the DoD CMM route.
FAR 52.204-21
- Basic Safeguarding of Covered Contractor Information Systems
- Applies to all Government Agencies
- Federal contract information
- Contractor Information Systems
- Fifteen requirements traceable to NIST 800-53 and 800-171
DFARS 252.204-7012
- Safeguarding covered defense information and cyber incident reporting
- Much larger set of requirements from NIST 800-171 and 800-171B
- Controlled Unclassified Information (CUI)
Common Need - Common Starting Point

It is these baseline recommendations that created the underpinnings of recommendations that were subsequently formulated in another series of NIST publications (NIST 800-171) that form the FAR 52.204-21 recommendations - which in turn - are a subset (or minimum set of requirements) from the entire (very long) list of requirements. Later, a supplementary standard NIST 800-171(a) was published with even MORE requirements - this time aimed at systems that have Controlled Unclassified Information resident on them.
In simple terms the FAR requirement in the Clause at 52.204-21 is a minimum requirement for ALL government contractors (and a required slowdown to subcontractors) that use their information systems ( contractor information system means an information system that is owned or operated by a contractor that processes, stores, or transmits Federal contract information) to create documents or data that are delivered under a government contract. "Federal contract information means information, not intended for public release, that is provided by or generated for the Government under a contract to develop or deliver a product or service to the Government, but not including information provided by the Government to the public (such as on public Web sites) or simple transactional information, such as necessary to process payments."
That broad definition means pretty much any computer used to create a contract deliverable item is covered. The exception would be something like a commercial items contract where off-the shelf goods are pulled from inventory and shipped to the government with the only information system use being preparing the shipping documents and invoice.
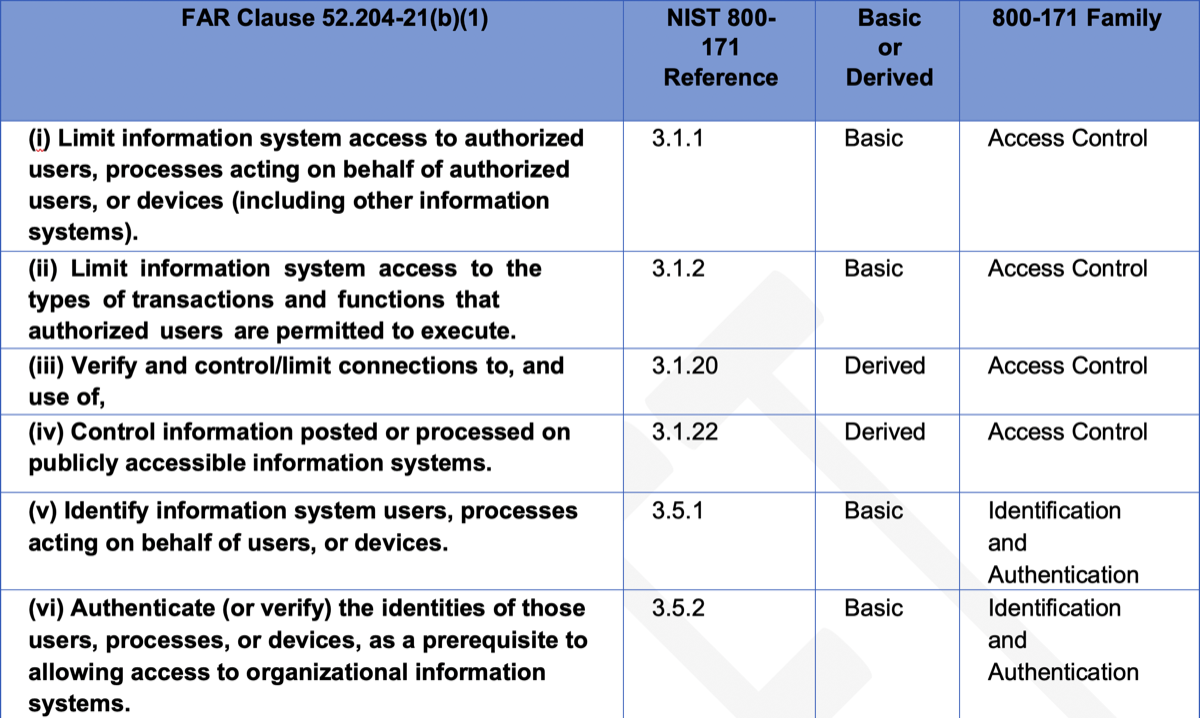
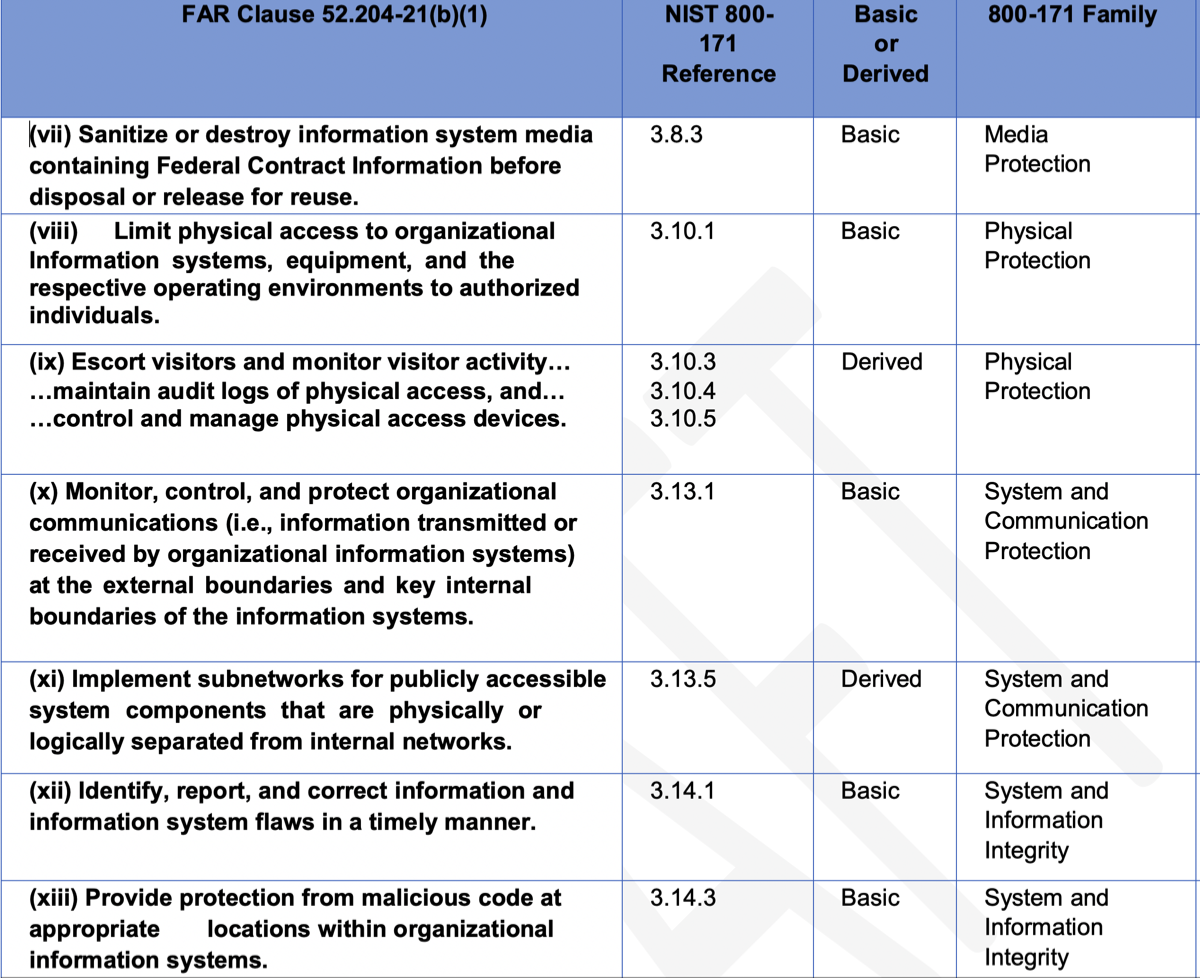
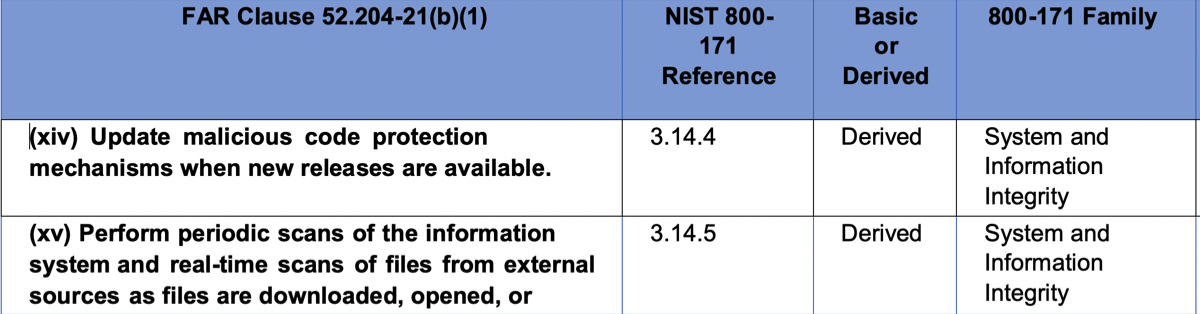
The 15 Essential Requirements of FAR 52.204-21